Google’s aspirational slogan has only been realized in a museum
After my last post about Amazon I received a question about dropping Google. Rather than respond individually, here I’m going to offer my 2c worth on a hodgepodge of related topics. I’m sure I will receive more feedback that this or that company I’ve recommended below has sociopathic CEOs or a history of repugnant campaign donations. You do know that CEOs are highly likely to be sociopaths and even psychopaths, don’t you? Well, welcome to Capitalism! In general, the object here is to de-couple from some of the worst and most powerful tech bro’s on the planet. And in this post I take on: Google, a company that long ago dumped its slogan: “don’t be evil.”
Google’s (as well as Yahoo’s, AOL’s, Microsoft’s and other biggies) primary attraction for most people is the free email. Who doesn’t like free? Unfortunately, most people are blissfully unaware that Google has been reading your emails for years. There are hundreds of companies that offer free email, but several I have personally used to replace Google email are: disroot.org; icloud.com; infomaniak.com; murena.io; proton.me; tutanota.com; vivaldi.net; and zohomail.com.
There are other companies providing low-cost (not free) email service hosted outside the US and not subject to Five Eyes surveillance (although the surveillance state is not really going to be deterred). A few I providers have tested are: countermail.com; mailbox.org; posteo.de; and startmail.com. Some are as inexpensive as 1€ (Euro) a month. You get what you pay for: in this case, better privacy.
Your choice of an email client is as important as the email provider you use. An email client is a specialized app that sends and receives email, maintains your contacts, and connects to your calendar. Apple’s Mail programs on MacOS and iOS are secure and private (and Apple makes email communications even more private with IP masking). On Linux, Claws, Evolution, Geary, and kMail are private and secure. On Windows, the built-in (Outlook “Lite”) client should not divulge data to third parties. Other apps that do not permit the contents of your mail folders to be sniffed by third parties include: Thunderbird (available on all desktop platforms and Android); emClient (Windows, Mac, and mobile); Betterbird (Windows, Mac, Linux); and Mailspring (Mac, Windows, Linux). In general you want an email client that uses only imap and smtp or the Windows exchange protocol.
Email clients that are not secure are those which collect passwords from your accounts and serve as intelligent front ends to multiple email accounts. These include programs like Spark Mail, BlueMail, Canary Mail, Edison, and even Microsoft Outlook for iOS. As friendly and capable as they are, these programs can cleverly organize your schedule and prioritize your inbox only by having complete access to both your passwords and the contents of your inbox. With the popularity of AI on the upswing, we’re going to see more and more of these apps popping up. They will all be threats to your privacy.
My recommendation: for best privacy, I’d use a paid, offshore email account with Thunderbird and PGP encryption or I’d use Proton Mail.
Cloud Storage
Another important feature for many Google users is their 15gb of free cloud storage. Once again, there are other companies that provide equivalent or even better services. You can replace Google cloud storage with: box.com; filen.io; infomaniak.com; mega.io; nextcloud (a network of providers who use a common set of apps); pcloud.com; or proton drive. One consideration is whether the provider offers cloud storage clients for each of the devices you use.
A caution: Microsoft offers a service called OneDrive, which MS Windows considers a “backup” device. This is either outlook.com’s “free” service offering 5gb or part of an Office365 subscription offering 100gb. Many people who think they are backing up their Windows systems are actually copying files to OneDrive storage. Blithely removing OneDrive could break something on Windows 11 if you’re not careful. My advice to anyone in this boat: first copy your data from OneDrive and then begin to systematically de-couple Windows from OneDrive.
My recommendation: Mega and pCloud.
Google Docs
Another feature for Google users is google sheets, google docs, and tools that are basically Microsoft Office in an online version. You can replace Google collaborative tools with LibreOffice, OnlyOffice, WPS Office, or the venerable Apache OpenOffice. If you need collaborative capabilities, try Collabora Online, an enterprise-ready version of LibreOffice.
My recommendation: LibreOffice.
Google Browser
For many people “Google” is synonymous with both their email provider, the browser they use to navigate the internet, and the search engine they use to look things up. In the following paragraph I am referring only to the browser you use to access the internet.
Google’s browser is used by 66.3% of users worldwide, Safari by 18%, Microsoft Edge by 5.33%, Firefox by 2.62%, Opera by 2%, and miscellaneous browsers 2%. Despite this apparent popularity — more likely that users generally don’t know they have other options — there are numerous privacy reasons to replace Google’s Chrome browser that I won’t go into here. Google has gifted the source code to its Chrome browser to the Open Source Chromium project, and Chromium serves as the basis for a number of third party browsers that have stripped out what is essentially Google spying and tracking code from their own versions. These Chrome-derived browsers can even use Chrome extensions. Microsoft’s Edge browser is one such example (although Microsoft has added their own spying and tracking mechanisms back into their code). Third party Chromium-derived browsers that respect your privacy better than Google include: Brave; Chromium; Iridium; Opera; and Vivaldi.
For Mac users, Safari is a great alternative, providing that you use a security extension to limit tracking by websites you browse.
Firefox is another completely separate browser with its own extensions and is regarded by many as more secure than Chromium (I tend to agree). Firefox has several spinoffs: GNU IceCat, LibreWolf and WaterFox are three of the more popular derivatives. The TOR browser is a hardened Firefox browser that uses the Onion routing protocol for supposedly secure surveillance-proof browsing, including to Dark Web sites. However, in my view it is doubtful that any system originally developed by the US military has anyone’s best interests in mind. So consider the Tor Browser to be insecure.
My recommendation: Brave and Firefox.
Search Engines
Finally, in common parlance “to Google” something now means “to search” something on the web. And with good reason. One study shows that Google searches represent over 90% of all searches worldwide, Bing 4%, Yandex 2%, Yahoo 1.3%, and Yandex (Russia) and Baidu (China) each less than 1%. Obviously, in Russia and China these numbers will be vastly different.
Google’s browser makes their own Google search engine the browser default, just as Microsoft makes Bing the default for its Edge browser and Brave makes its own Brave Search engine their own browser’s default. But using other search engines is simply a matter of navigating to a URL such as duckduckgo.com, search.brave.com, startpage.com, or qwant.com. You can also replace Google’s search engine in any browser by going into the browser settings and changing the default search engine to something more secure.
Just as a browser can slurp up your personal information without permission, a search engine may do the same by recording your search terms and IP address in logs that (1) are used to track your consumer preferences; or (2) can be subpoenaed or simply handed over to authorities without even a warrant. If you are concerned that your search on “Israeli genocide” or “abortion providers” might come back to haunt you, you just might want to replace your default search engine.
My recommendation: duckduckgo, brave search, and startpage.

 Ach nein! Was meinst Du denn? Weder von uns ist ein Nazi!
Ach nein! Was meinst Du denn? Weder von uns ist ein Nazi!
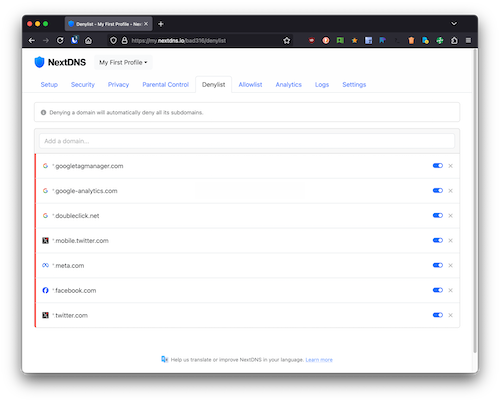
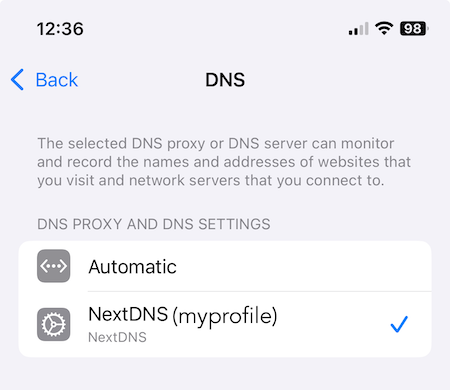
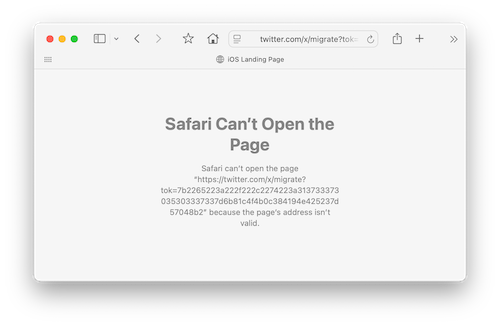
 If you wouldn’t vote for the fascist on the left, why are you using the fascist on the right’s social network?
If you wouldn’t vote for the fascist on the left, why are you using the fascist on the right’s social network?